It’s a common mistake to think of the cost of insider fraud as only the amount of money that was stolen, substantial as it may be. Unfortunately, this is FAR from the truth.
In this blog post, I would like to address the actual effects of “bad insiders.” Not only the direct damage they cause, but the added outcomes of entrusting the integrity of the payment process in their hands.
According to the Ponemon Institute’s 2020 Cost of Insider Threats Global Report, “The frequency and cost of insider threats have increased dramatically over the course of two years. For example, the overall cost of insider threats is rising, with a 31% increase from $8.76 million [per occurrence] in 2018, to $11.45 million in 2020.”
Internal Processes Just Aren’t Enough
When asked about anti-fraud measures, CFOs usually state “internal processes” as their main line of defense. These would most likely include dual signatures, phone calls, manual review of documents, etc. The inherent flaw in this scenario is: “Who’s guarding the guards?”
J.P. Morgan’s 2020 Payments Fraud and Control Survey Report from the Association for Financial Professionals’ (AFP) says that, “despite the controls and processes organizations have put in place to safeguard their payment systems and minimize instances of fraud, it is evident that perpetrators of these crimes have not been discouraged and are still able to infiltrate payment systems.”
We often associate cyber-attacks with information security, where the risk may consist of the loss of personal data, legal and compliance issues, and possible monetary punitive damages. In the case of payment fraud (both external and internal), however, perpetrators simply tap into the outbound monetary flow, thus diverting funds into their own accounts.
According to research, fraudulent attacks by insiders are the “most harmful” to organizations, both in terms of the monetary losses and related collateral damages: loss of reputation, legal actions, personal steps against managers, etc.
The statistics on insider fraud aren’t good: According to PwC’s 2020 Global Economic Crime and Fraud Survey, “Nearly half of reported incidences resulting in losses of US$100 million or more were committed by insiders.”
The Potential Damage
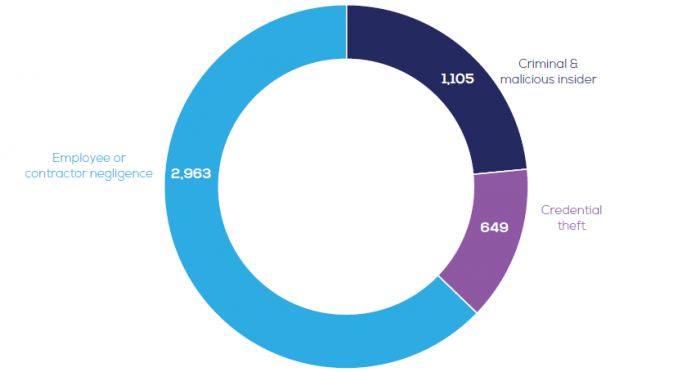
Ponemon Institute’s research defined three examples of Insider Threats:
- A careless or negligent employee or contractor
- A criminal or malicious insider
- Credential theft (aka, imposter risk)
The the statistics of each threat within the report look like this:
Furthermore, according to the Ponemon Institute, the total value (or damage) of criminal insider fraud should include the following:
- Monitoring and surveillance: Activities that enable an organization to reasonably detect and possibly deter insider incidents or attacks.
- Investigation: Activities necessary to thoroughly uncover the source, scope, and magnitude of one or more incidents.
- Escalation: Activities taken to raise awareness about actual incidents among key stakeholders within the company.
- Incident response: Activities relating to the formation and engagement of the incident response team.
- Containment: Activities that focus on stopping or lessening the severity of insider incidents or attacks.
- Ex-post response: Activities to help the organization minimize potential future insider-related incidents and attacks.
- Remediation: Activities associated with repairing and remediating the organization’s systems and core business processes.
Taking all the above into consideration, the TOTAL cost of insider asset misappropriation schemes depicts a totally different and much more alarming picture:
- The cost of credential theft averages $871,686.
- The cost of a criminal or malicious insider averages $755,760.
- The cost of a careless or negligent employee or contractor averages $307,111.
A Better Way to Combat Insider Fraud
The basic nature of internal processes leaves constant temptation dangling before accounting teams, whether inputting data or overseeing the payment process.
The best way to battle insider fraud is by removing the temptation, altogether. Block the opportunity to manipulate account information and the option to change bank account details during the payment run process.
We advise our clients to use third party data sources that are not susceptible to manipulation by insiders. Additionally, utilizing technology can allow the AP manager to control the entire process and monitor every payment made.
Conclusion
As shown above, the problem of “bad insiders” should concern every financial manager because the consequences are dire. And the lure just continues to grow, especially in times of crisis. Research shows this phenomenon as a growing threat to corporations, with numbers growing both in frequency and the amounts of money involved.



